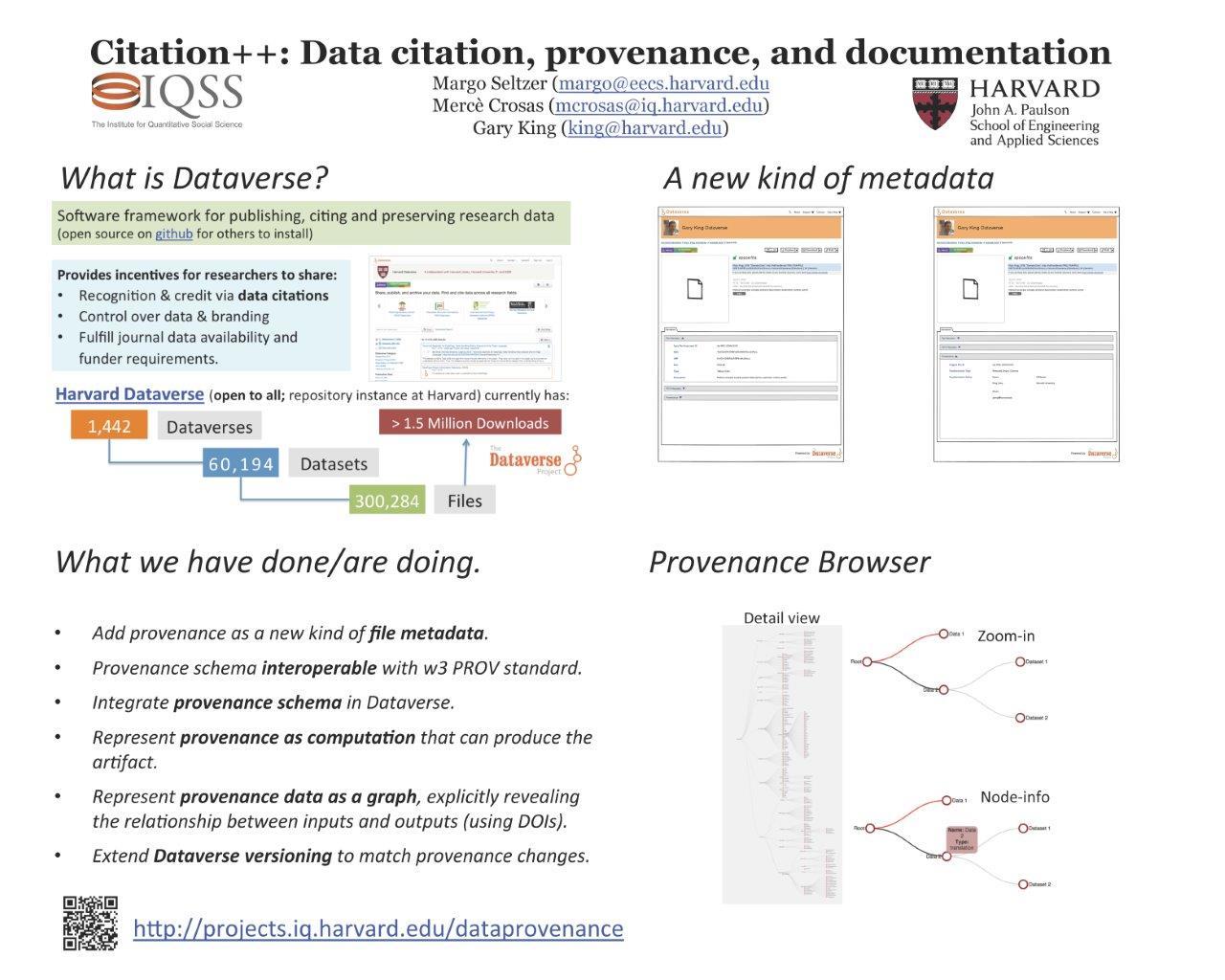
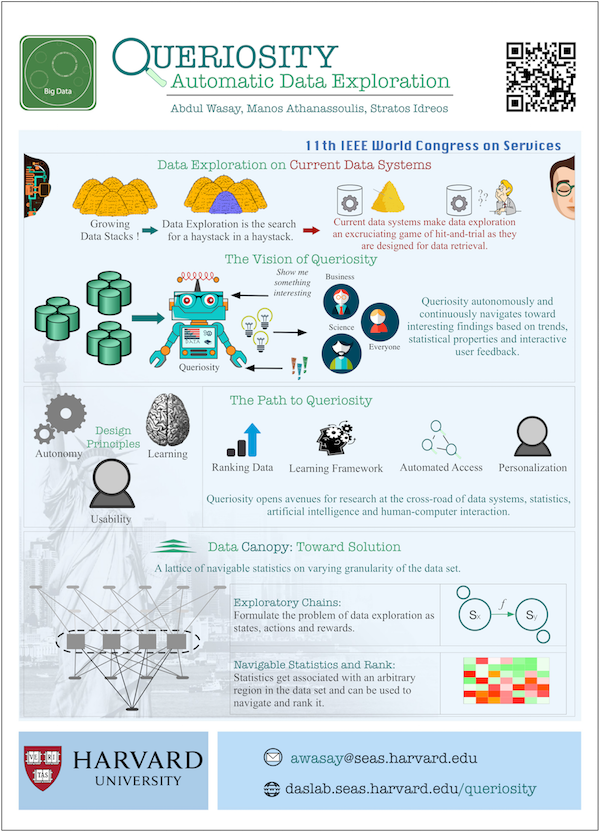
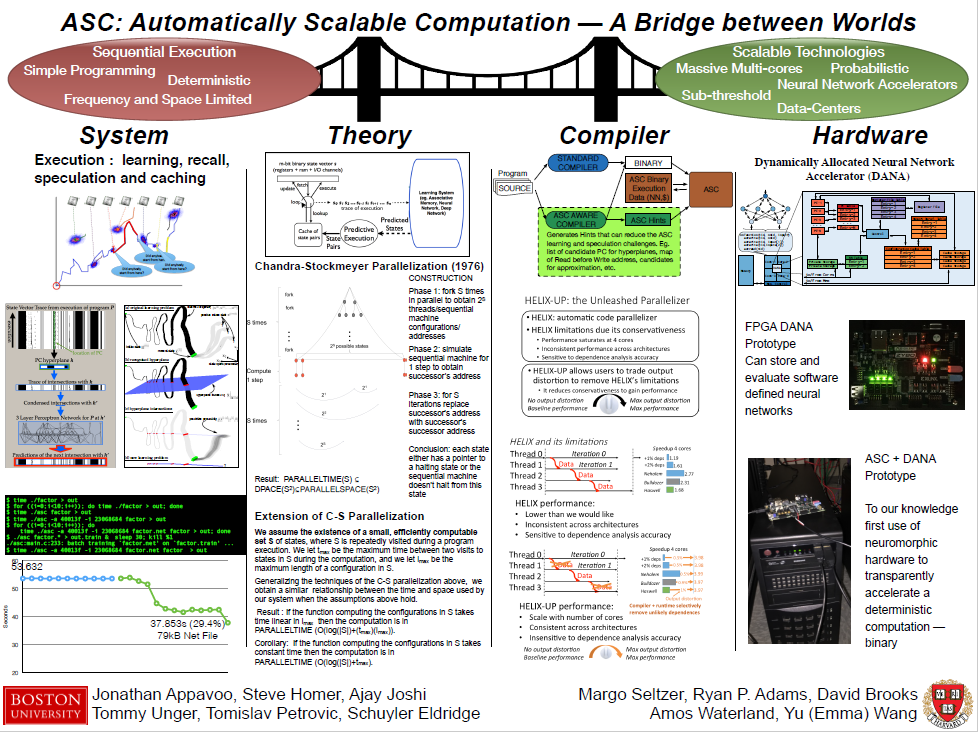
Recent Publications
- Scalable Bayesian Rule Lists
- A Crowdsourcing Approach to Collecting 399 Tutorial Videos on Logarithms
- Polaris: Faster Page Loads Using Fine-grained Dependency Tracking
- Designing Access Methods: The RUM Conjecture
- Adaptive Indexing over Encrypted Numeric Data
- Polaris: Faster Page Loads Using Fine-grained Dependency Tracking
- Automatically Scalable Computation
- A scalable distributed graph partitioner
- Towards general-purpose neural network computing
- Recent advances in computer architecture: the opportunities and challenges for provenance
- LLAMA: Efficient graph analytics using Large Multiversioned Arrays
- A Scalable Distributed Graph Partitioner
- ASC: Automatically scalable computation
- A Framework for Incentivizing Deep Fixes
- A primer on provenance
- Avoiding the top 10 software security design flaws
- Programmable smart machines: A hybrid neuromorphic approach to general purpose computation
- Accelerating MCMC via parallel predictive prefetching
- Computational caches
- Automated Use of Electronic Health Record Text Data To Improve Validity in Pharmacoepidemiology Studies